I recently attended a workshop on Spatial Computing for C-IED (Counter-Improvised Explosive Device) organised by the Netherlands Aerospace Centre (NLR) and the European Defence Agency (EDA). The three-day event was very informative and interactive and included an introduction to spatial computing, an overview of C-IED work and practices, and various sessions to discuss issues and the art of the possible based on spatial computing for C-IED.
In 2003, MIT researcher Simon Greenwold defined spatial computing as “human interaction with a machine in which the machine retains and manipulates referents to real objects and spaces.” So whether that’s a 2D map on a tablet screen, overlaid augmented reality on a mobile device or a full virtual environment representing a real location, there are many applications for spatial computing in C-IED.
IEDs are tactical weapons that, when employed, can have effects to a strategic level. They can be combined with differing substances, such as ammunition, chemical, biological, radiological and nuclear (CBRN) substances to create complex attacks. The effects of IEDs are widely felt in a number of ways:
- Restricting freedom of movement for all in the locality
- Creating profound psychological effects
- Spreading insecurity
- Effecting support for operations beyond the battlefield from local and allied nations’ populations
The prominence of IEDs has risen with conflicts where they were one of the chosen weapons of adversaries, but they are not new. Historical records from the World Wars give accounts of IEDs used as booby traps in trenches.
The aim of C-IED is to prevent the device being detonated and stay on the “left of the boom,” as shown in this diagram:
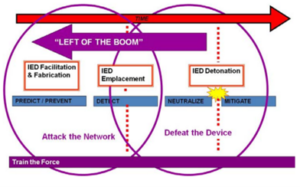
‘Left of the boom’ from Attacking the IED Network NDIA Global EOD Conference CAPT Frederick Gaghan, USN 05 May 2011
Efforts to counter IEDs and prevent their many effects are made up of multiple disciplines, which are used in three stages, along with a supporting foundation.
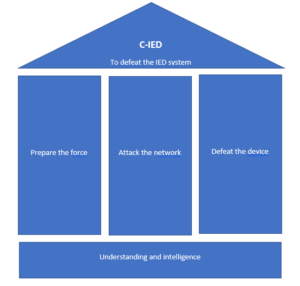
The C-IED approach with supporting pillars from NATO Standard AJP-3.15 Allied Joint Doctrine for Countering Improvised Explosive Devices
Preparing the force is all about training the soldiers on how to counter IEDs, understanding the methods and reasoning of their use and being ready at any time for any stage of C-IED activities. Attacking the network is working to infiltrate, disrupt and capture those involved in setting, financing, building and publicising IEDs. Defeating the device is the action of disarming and retrieving an IED when it’s discovered.
Augmented and virtual realities (AR/VR) can be used in training (for example, on the defusal of an IED) and to aid in the planning phase, in essence to replace PowerPoint as the main way of conveying all the findings of the “attack the network” phase. For deployment into the field, hardware will need to be more robust, but the frontline user will find it extremely useful if available.
In preparing the force and defeating the network, change detection using EO (earth observation) data can potentially be exploited more. Sources such as LiDAR detect topography changes, so changes to banks or culverts can be captured routinely by convoys or UAS (unmanned autonomous systems) flown/driven along routes. A change of surface, such as new objects or road metalling, can be seen in change detection based on video imagery, for example. In preparing the force, the identification of potential pinch points, such as a bridge or a marketplace on market day, can be made ahead of deployment using geographic analysis on different data sources.
There is obviously a large workload on the soldiers in a convoy, so rather than manually taking notes, natural language processing could be used to, for example, identify comments of “man in red waiting by phone box” made on different convoys. This capability is already being utilised in public safety, such as with Hexagon OnCall Dispatch | Smart Advisor.
The geographic networks of people are relevant in defeating the network. Do people pass the same place in quick succession, but not at the same time, to exchange information or materials via dead letter drops? What are the routes that are repeated? This is of relevance for adversaries and war fighters alike. Potentially, device tracking, such as a suspect phone appearing in a new locality, can help follow the planning phase of IED activities.
If needed, during the defeat the device stage, a safety circle is envisaged — either from the convoy vehicle of the area being jammed via electronic counter measures or the area potentially affected by a blast zone around buildings (that would require evacuation of locals). The line of sight for radios and communications to relay masts, etc., can be depicted in near-real time, helping the war fighter identify potential trigger locations via remote means.
Either during a convoy survey or after a blast event, rapid LiDAR scanning of the area via handheld or airborne unmanned vehicles will create a permanent record of the environment for forensics and for training datasets. Systems such as the Leica BLK can provide this quick data capture.
Streamlining and making reporting and data collection easier via digitisation of workflows will help increase information assurance throughout the C-IED.
Geography is often used as the common base on which to share information between convoys or allies. As with many parts of defence, C-IED in theatre suffers from data deluge, in volume and number of sources. On top of that, the electronic environment is often limited, congested, or non-existent as vehicles travel, meaning convoys need to operate in isolation.
Spatial computing can help advance learning, detect thinking and prevent disruption via the analysis and interrogation of data. The combination of geography and data sources provides answers greater than either part alone, making it possible to prevent IED detonation in first place and stay left of the boom.
To learn more about Hexagon’s defence solutions and capabilities, visit our defence industry page.